First off, if you are still pondering the age old question “Should my users be local admin or not” I’m gonna help you right here: No, No, a Thousand Times No。 The only good reason I can think of for letting your users be local administrators is if you have too much money & time on your hands and could use a ransomware or two this year to slow down production. I’m not gonna spend more time on it here but if you want more input Sami Laiho has some really great posts and talks about the subject that really removes all doubt. So now that we’ve resolved the question on local admin or not, the next questions comes to how we go about doing this in Intune/Endpoint Manager. Intune provides a great way of doing so using Autopilot, but since autopilot is easier said than done for a lot of people & situations there might be a lot of devices with users ending up as local admin
Note: This is for Azure AD Only / Cloud Only Devices
P.S There will be some discussions on LAPS / One time passwords at the last chapter
Solution
So let’s head on to the how’s about removing local admin rights, and it’s really not magical or revolutionary. So as some of you may have noted Intune does provide a profile that allows you to modify the local admin group, but it’s not super easy to get around to understand and since I’ve noted some people get errors even when creating the profile and others get tons of errors in the Intune Portal
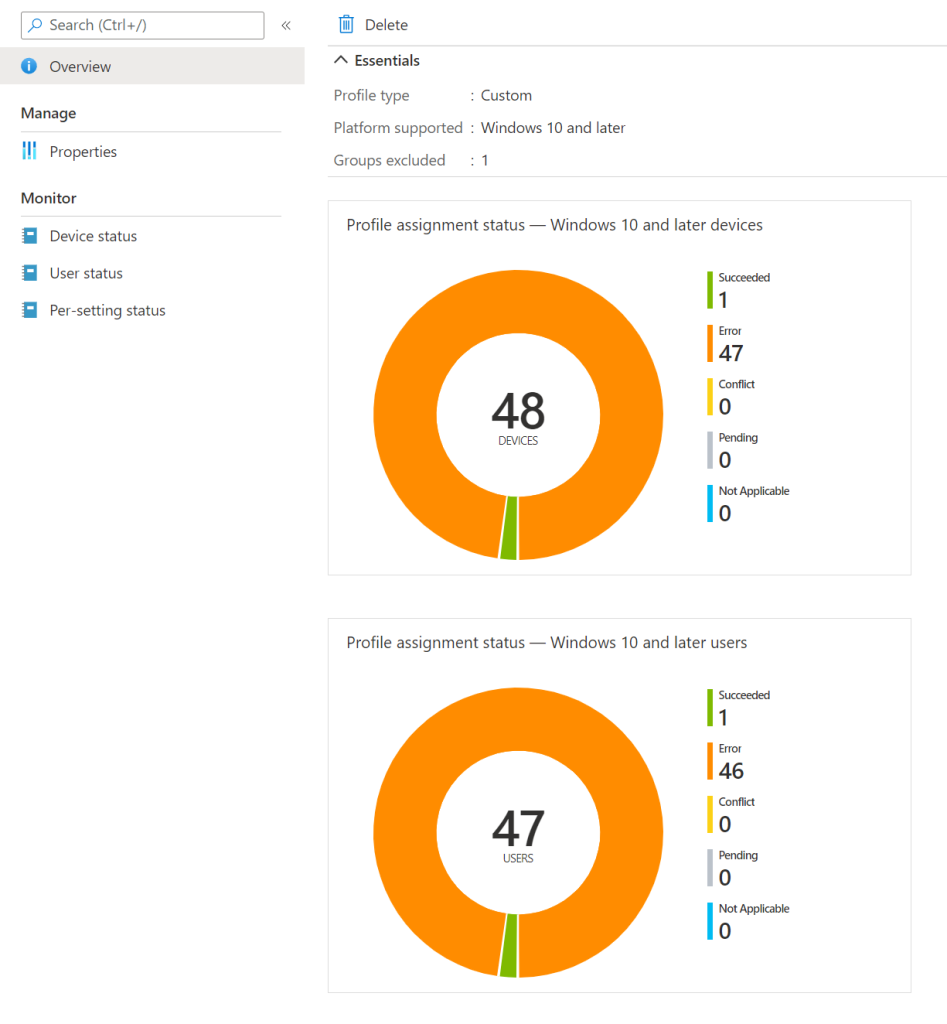
The reason for the policy generating errors or generally not yielding the results people wants has been varying, but one of the most common one’s has to do with the OS language being different on different machines, and to this my colleague came up with a simple and brilliant solution
So the goal of today is to create a policy that removes any user from the local administrator group that works on all devices without generating any errors (in as few steps as possible), and to do this we’re going to do this without scripts only using Intune profiles
What we need
- An Azure AD joined device
- To view the contents of the local administrator group
- 2 Intune Profiles
- 1 profile that dictates the contents of the local administrator group
- 1 profile that renames the local administrator account
Thats it! Only a few steps to get this to work
Azure AD joined device
Okey, to start this off we’re gonna take a look at the contents of the local administrators group on an Azure AD joined device. You can access the local administrators group with the shortcut lusrmgr.msc
Make sure you have local administrative access to the device
- Hit the Windows Button and search for lusrmgr.msc, right click Run as administrator
- Open Groups
- Open Administrators group (Different name in depending on OS language)
When we open the group its gonna look like this:

There’s going to be the local administrators account, the User Account that is current local administrator and 2 long SID’s
First off, the local administrator account needs to be there, we cannot remove it from the Administrators group but as this is an Intune / Azure AD joined device its disabled by default and has no password
Then we have the User Account that has enrolled the device, which if its not an Autopilot device will automatically become local administrator
Then we have the 2 longs SID’s that will be on all Azure AD joined devices per default,
One of them is the Azure AD Role group for “Global Administrator” and the other one is the Azure AD Role group for “Local device administrators”. So if we want Global administrators and the group for Local device administrators to continue to work, we need to keep them in the local administrators group
We can view the users in the local device administrators role group in Azure AD
- Open Azure AD
- Navigate to the Devices blade
- Navigate to Device settings
- Click on Manage Additional local administrators on all Azure AD joined devices at the bottom of the page
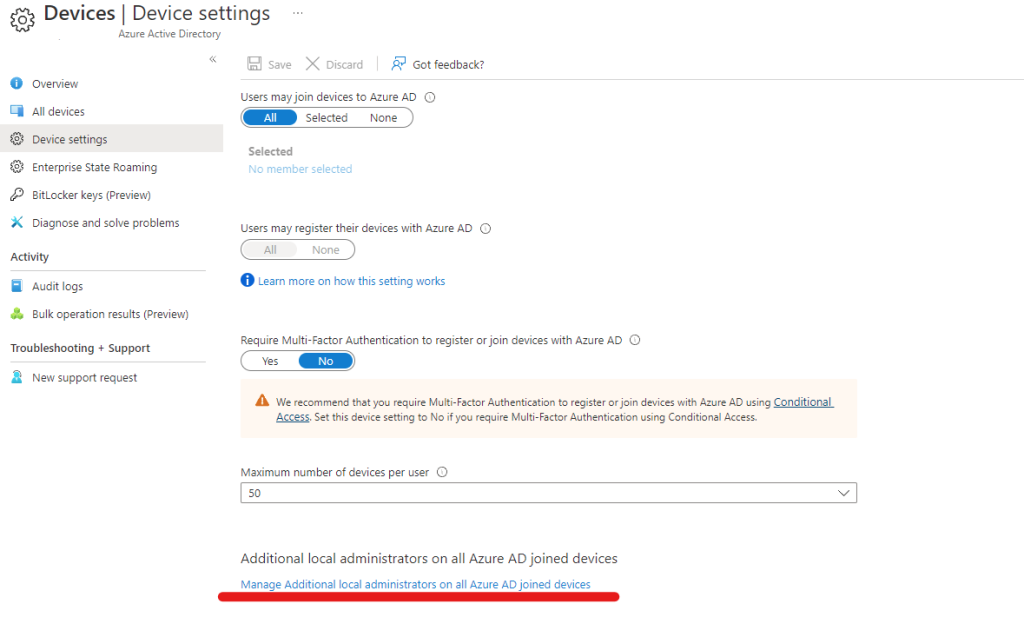
Depending of if you used this Group up until now or not this maybe empty or populated with the correct administrators for your devices
So if we wanna keep both of these groups as local administrators we can just copy them from our Azure AD joined device. But to find out which is which we will need to resort to our lord and savior; PowerShell
Before we open PowerShell make sure to add at least one User to the Additional local administrators on all Azure AD joined devices page, if not it won’t show up
- Open PowerShell
- Make sure you have the Module AzureAD installed
- If you need to install the PowerShell module make sure PowerShell is started as Administrator
- Type Install-Module AzureAD
- Accept the install
- Type Connect-AzureAD
- Sign in with an account with privilege’s to read the AzureAD Directory
- Type Get-AzureADDirectoryRole (More information on the command and on the module can be found on the Microsoft Docs)
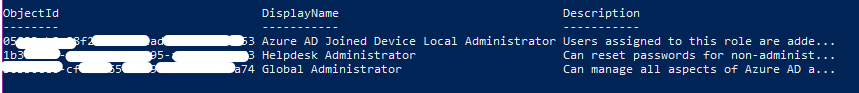
Now we’re going to convert those object ID’s to SID’s using a awesome function that Oliver Kieselbach made a while back.
Automation Account Script
| 12345678910111213141516171819202122232425262728 | Function Convert-AzureAdObjectIdToSid { <# .SYNOPSIS Convert an Azure AD Object ID to SID .DESCRIPTION Converts an Azure AD Object ID to a SID. Author: Oliver Kieselbach (oliverkieselbach.com) The script is provided “AS IS” with no warranties. .PARAMETER ObjectID The Object ID to convert #> param([String] $ObjectId) $bytes = [Guid]::Parse($ObjectId).ToByteArray() $array = New-Object ‘UInt32[]’ 4 [Buffer]::BlockCopy($bytes, 0, $array, 0, 16) $sid = “S-1-12-1-$array”.Replace(‘ ‘, ‘-‘) return $sid } $objectId = “INSERT OJBECT ID FROM AZURE HERE”$SID = Convert-AzureAdObjectIdToSid -ObjectId $objectIdWrite-Output $SID |
- Copy the code to a PowerShell ISE Window (or ISE or IDE of your choice)
- Edit the Object ID on Line 26 to the Object ID returned in the previous steps for Azure AD Joined Device Local Administrator and Global Administrator (one at the time)
- Run the Script and the same SID’s we saw in the local administrators group should be returned!
Intune Profiles
Now that we have all the information from the local administrators group, let’s head on to Intune to create our 2 profiles
As I mentioned before, we’re gonna try to get this done without errors and with multiple language support. So one of our issues we’re gonna run into later is when we create the profile that dictates the content of the local administrator group, we’re gonna need to know the name of the local administrators account, because as mentioned windows requires the local admin account to be in the local admin group. So first off we’re gonna create a policy that renames the local admin account so its the same on all devices
In Intune:
- Navigate to Devices
- Navigate to Windows
- Navigate to Configuration profiles
- Chose Create profile
- Platform: Windows 10 and later Profile Type: Settings catalog
- Chose a Fitting name for your profile, I chose “Rename Local Administrator Account” but it doesn’t matter
- Chose Add Settings
- Search for Local Policies Security Options
- Chose Local Policies Security Options
- When the list appears chose Accounts Rename Administrator Account
- Then rename it to whatever you want it called, I chose “Administrator” but it doesn’t matter
- Chose Next
- Assign it
Okey, now we have a the same name of the local administrator on all devices, lets move on to creating the Users and Groups profile
In Intune:
- Navigate to Endpoint Security
- Navigate to Account protection
- Chose Create profile
- Platform: Windows 10 and later Profile Type: Local user group membership
- Chose a Fitting name for your profile, I chose “Local Administrator Group Membership” but it doesn’t matter
- For Local Group: Select Administrators
- Then for Group and user action we have 3 alternatives, before we move on lets explain them
- Add (Update) – Choosing this option will just add whatever user you chose to the group you chose, simple
- Remove (Update) – This will remove the users you chose, but you have to specify exactly which one, so we cant use this to remove our users from local administrator
- Add (Replace) – This will remove all users in the group you specify and add the users / groups you specify
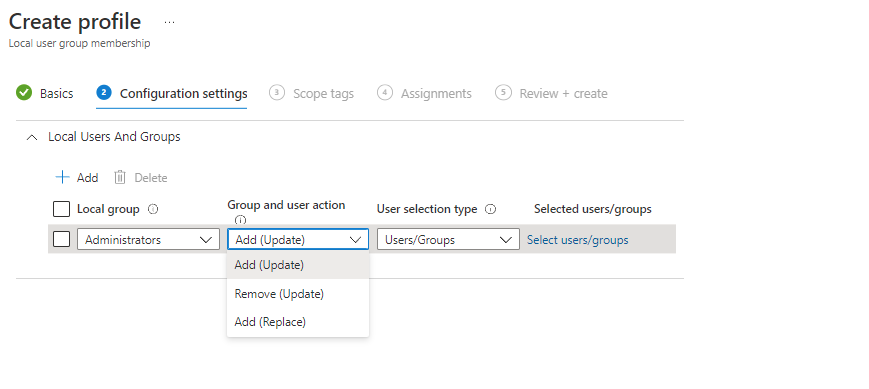
- Chose Add (Replace) as we already have our full list of users/groups we want, and what we are trying trying to achieve is to make sure nothing else is in the Local Administrators group this fits us perfectly
- User selection type: Manual
- Click Add users
- Add the 2 SID’s we extracted earlier and the username of the Local Administrators account we decided on in the previous profile

- Chose OK then Next
- Assign it
Done!
I recommend assigning it to a test device and making sure that you end up with your local admin account, the group SID’s but no end user.