TIPS: Scroll down this post and try soltuion#2 would be a easy and fast way to fix this.
Solution #1
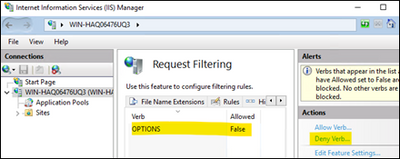
Penetration tools may alert if IIS server is accepting requests with HTTP OPTIONS method. This is because the response to these requests may reveal what other methods are supported by the web server.
Warning: Disabling OPTIONS may have unintended consequences like CORS preflight requests to break. Please test the applications thoroughly after making the change below.
Follow the steps below to disable OPTIONS method.
- Open IIS Manager
- Click the server name
- Double click on Request Filtering
- Go to HTTP Verbs tab
- On the right side, click Deny Verb
- Type OPTIONS. Click OK
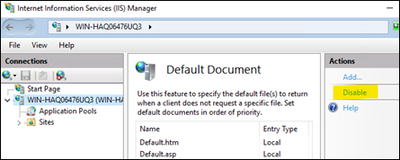
Penetration tools may also raise an alarm if the default IIS page is still available in your server. This page comes by default when you install Web Server role.
Warning: Disabling the default page of a web application may cause unwanted results. Please make sure to test the application thoroughly after following the steps below.
Follow the steps below to disable it so this vulnerability don’t come up in the reports anymore.
- Open IIS Manager
- Click the server name
- Double click on Default Document
- On the right side, click “Disable”
Solution #2
Just delete the iisstart.* pages at c:\inetpub\wwwroot and it should solve the problem.