The best way is to have this done by a free tool called “IIS Crypto” from the Nartac Software. You can download the tool from here.
Below, is a way to get this done manually. but it’s not recommended.
SSLv3 is an obsolete protocol, the main attack vector on which, at the time of writing, is an attack called POODLE. Disabling SSLv3 is the ultimate solution to mitigate security risks. Another option suitable for servers that critically require SSLv3 support is a signalizing TLS_FALLBACK_SCSV cipher suite that allows to keep SSLv3 enabled, but prevents downgrade attacks from higher protocols (TLSv1 =< ). Unfortunately, at the time of writing, Microsoft didn’t yet add support for TLS_FALLBACK_SCSV in SChanel. Therefore, disabling SSLv3 is the only mitigation measure a certificate administrator can apply against POODLE in case of a Windows Server.
- Open registry editor:Win + R >> regedit
- Navigate to:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Protocols\
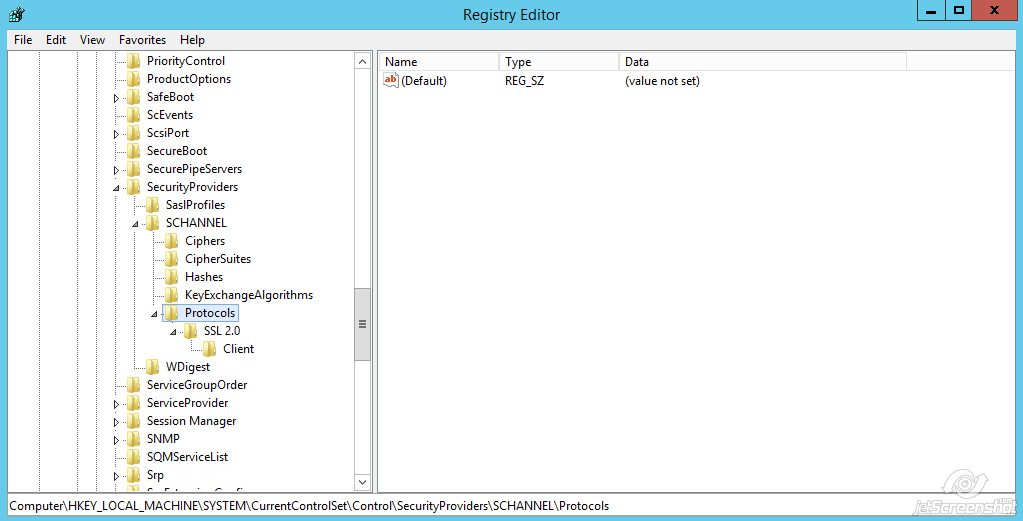
- By default, there should be only one key presented “SSL 2.0”. We need to create a new one for SSLv3Right-click on Protocols >> New >> KeyName the key ‘SSL 3.0’
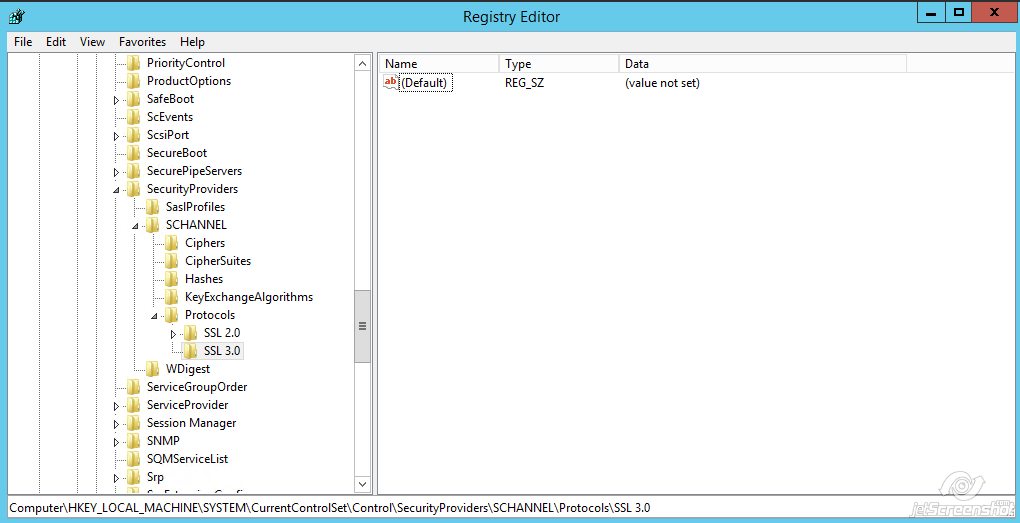
- Right-click on SSL 3.0 >> New >> Key
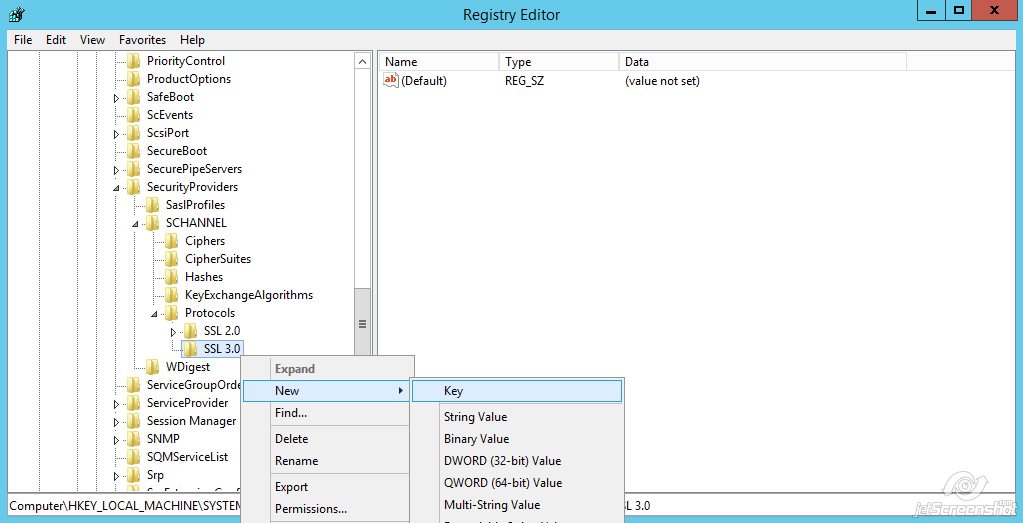 Name the key ‘Server’
Name the key ‘Server’ - Right-click on Server >> New >> DWORD (32-bit) Value
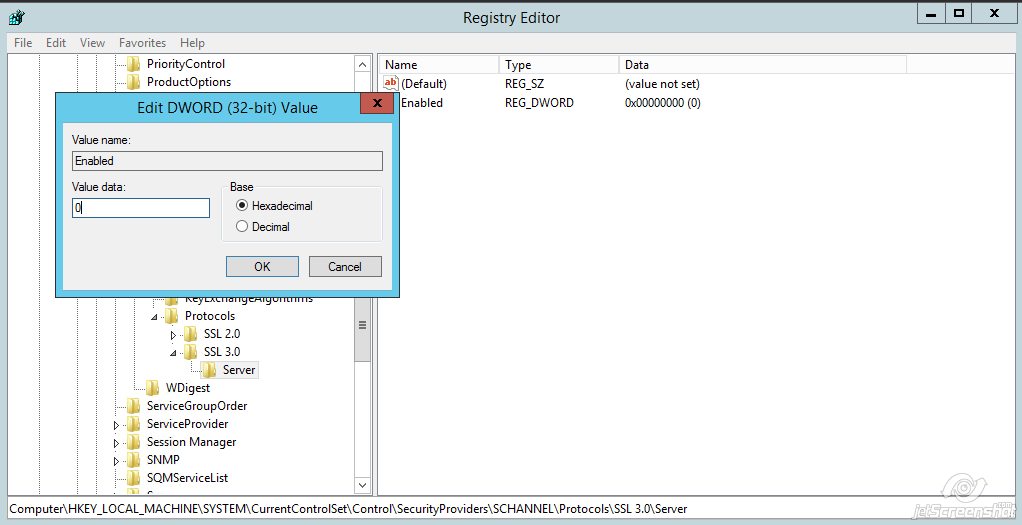
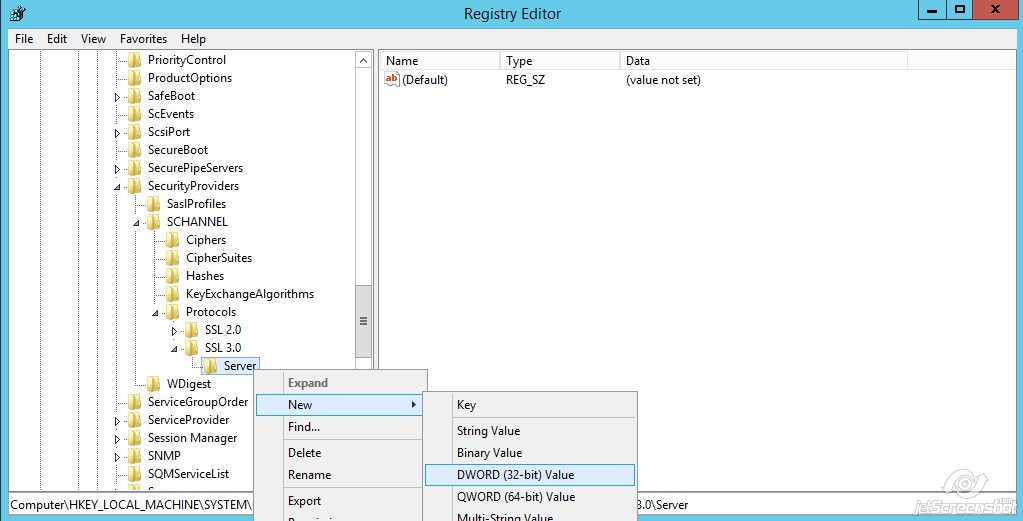 Name the value ‘Enabled‘
Name the value ‘Enabled‘ - Double-click the Enabled value and make sure that there is zero (0) in the Value Data field >> click OK
- You may need to restart Windows Server to apply the changes.