Step 1: Retrieve the PRT status by using dsregcmd /status
- Open a Command Prompt window. NoteTo get the Primary Refresh Token (PRT) status, open the Command Prompt window in the context of the logged-in user.
- Run
dsregcmd /status.The “SSO state” section provides the current PRT status.If the AzureAdPrt field is set to NO, there was an error acquiring the PRT status from Azure AD. - If the AzureAdPrtUpdateTime is more than four hours, there’s likely an issue with refreshing the PRT. Lock and unlock the device to force the PRT refresh, and then check to see whether the time has been updated.
+----------------------------------------------------------------------+
| SSO State |
+----------------------------------------------------------------------+
AzureAdPrt : YES
AzureAdPrtUpdateTime : 2020-07-12 22:57:53.000 UTC
AzureAdPrtExpiryTime : 2019-07-26 22:58:35.000 UTC
AzureAdPrtAuthority : https://login.microsoftonline.com/96fa76d0-xxxx-xxxx-xxxx-eb60cc22xxxx
EnterprisePrt : YES
EnterprisePrtUpdateTime : 2020-07-12 22:57:54.000 UTC
EnterprisePrtExpiryTime : 2020-07-26 22:57:54.000 UTC
EnterprisePrtAuthority : https://corp.hybridadfs.contoso.com:443/adfs
+----------------------------------------------------------------------+
Step 2: Find the error code
From the dsregcmd output
Note
The output is available from the Windows 10 May 2021 update (version 21H1).
The “Attempt Status” field under the “AzureAdPrt” field will provide the status of the previous PRT attempt, along with other required debug information. For earlier Windows versions, extract the information from the Azure AD analytics and operational logs.Copy
+----------------------------------------------------------------------+
| SSO State |
+----------------------------------------------------------------------+
AzureAdPrt : NO
AzureAdPrtAuthority : https://login.microsoftonline.com/96fa76d0-xxxx-xxxx-xxxx-eb60cc22xxxx
AcquirePrtDiagnostics : PRESENT
Previous Prt Attempt : 2020-07-18 20:10:33.789 UTC
Attempt Status : 0xc000006d
User Identity : [email protected]
Credential Type : Password
Correlation ID : 63648321-fc5c-46eb-996e-ed1f3ba7740f
Endpoint URI : https://login.microsoftonline.com/96fa76d0-xxxx-xxxx-xxxx-eb60cc22xxxx/oauth2/token/
HTTP Method : POST
HTTP Error : 0x0
HTTP status : 400
Server Error Code : invalid_grant
Server Error Description : AADSTS50126: Error validating credentials due to invalid username or password.
From the Azure AD analytics and operational logs
Use Event Viewer to look for the log entries that are logged by the Azure AD CloudAP plug-in during PRT acquisition.
- In Event Viewer, open the Azure AD Operational event logs. They’re stored under Applications and Services Log > Microsoft > Windows > AAD. NoteThe CloudAP plug-in logs error events in the operational logs, and it logs the info events in the analytics logs. The analytics and operational log events are both required to troubleshoot issues.
- Event 1006 in the analytics logs denotes the start of the PRT acquisition flow, and event 1007 in the analytics logs denotes the end of the PRT acquisition flow. All events in the Azure AD logs (analytics and operational) that are logged between events 1006 and 1007 were logged as part of the PRT acquisition flow.
- Event 1007 logs the final error code.
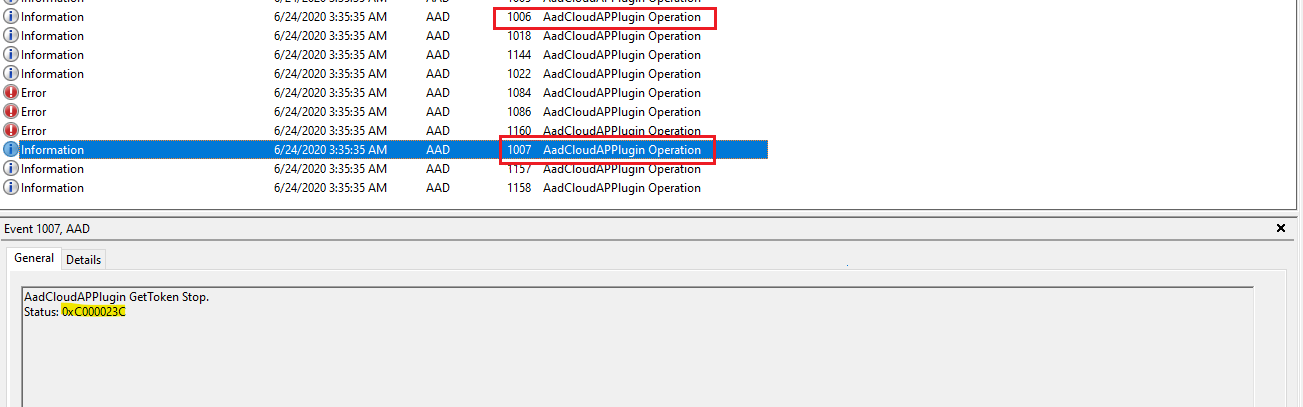
Step 3: Troubleshoot further, based on the found error code
| Error code | Reason | Resolution |
|---|---|---|
| STATUS_LOGON_FAILURE (-1073741715/ 0xc000006d) STATUS_WRONG_PASSWORD (-1073741718/ 0xc000006a) | The device is unable to connect to the Azure AD authentication service.Received an error response (HTTP 400) from the Azure AD authentication service or WS-Trust endpoint. Note: WS-Trust is required for federated authentication. | If the on-premises environment requires an outbound proxy, the IT admin must ensure that the computer account of the device can discover and silently authenticate to the outbound proxy.Events 1081 and 1088 (Azure AD operational logs) would contain the server error code for errors originating from the Azure AD authentication service and error description for errors originating from the WS-Trust endpoint. Common server error codes and their resolutions are listed in the next section. The first instance of event 1022 (Azure AD analytics logs), preceding events 1081 or 1088, will contain the URL that’s being accessed. |
| STATUS_REQUEST_NOT_ACCEPTED (-1073741616/ 0xc00000d0) | Received an error response (HTTP 400) from the Azure AD authentication service or WS-Trust endpoint. Note: WS-Trust is required for federated authentication. | Events 1081 and 1088 (Azure AD operational logs) would contain the server error code and error description for errors originating from Azure AD authentication service and WS-Trust endpoint, respectively. Common server error codes and their resolutions are listed in the next section. The first instance of event 1022 (Azure AD analytics logs), preceding events 1081 or 1088, will contain the URL that’s being accessed. |
| STATUS_NETWORK_UNREACHABLE (-1073741252/ 0xc000023c) STATUS_BAD_NETWORK_PATH (-1073741634/ 0xc00000be) STATUS_UNEXPECTED_NETWORK_ERROR (-1073741628/ 0xc00000c4) | Received an error response (HTTP > 400) from the Azure AD authentication service or WS-Trust endpoint. Note: WS-Trust is required for federated authentication.Network connectivity issue to a required endpoint. | For server errors, events 1081 and 1088 (Azure AD operational logs) would contain the error code from the Azure AD authentication service and the error description from the WS-Trust endpoint. Common server error codes and their resolutions are listed in the next section.For connectivity issues, event 1022 (Azure AD analytics logs) will contain the URL that’s being accessed, and event 1084 (Azure AD operational logs) will contain the sub-error code from the network stack. |
| STATUS_NO_SUCH_LOGON_SESSION (-1073741729/ 0xc000005f) | User realm discovery failed because the Azure AD authentication service was unable to find the user’s domain. | The domain of the user’s UPN must be added as a custom domain in Azure AD. Event 1144 (Azure AD analytics logs) will contain the UPN provided.If the on-premises domain name is non-routable ([email protected]), configure an Alternate Login ID (AltID). References: Prerequisites; Configure Alternate Login ID. |
| AAD_CLOUDAP_E_OAUTH_USERNAME_IS_MALFORMED (-1073445812/ 0xc004844c) | The user’s UPN isn’t in the expected format. Notes:For Azure AD-joined devices, the UPN is the text that’s entered by the user in the LoginUI.For hybrid Azure AD-joined devices, the UPN is returned from the domain controller during the login process. | User’s UPN should be in the internet-style login name, based on the internet standard RFC 822. Event 1144 (Azure AD analytics logs) will contain the UPN provided.For hybrid-joined devices, ensure that the domain controller is configured to return the UPN in the correct format. In the domain controller, whoami /upn should display the configured UPN.If the on-premises domain name is non-routable ([email protected]), configure Alternate Login ID (AltID). References: Prerequisites; Configure Alternate Login ID. |
| AAD_CLOUDAP_E_OAUTH_USER_SID_IS_EMPTY (-1073445822/ 0xc0048442) | The user SID is missing in the ID token that’s returned by the Azure AD authentication service. | Ensure that the network proxy isn’t interfering with and modifying the server response. |
| AAD_CLOUDAP_E_WSTRUST_SAML_TOKENS_ARE_EMPTY (–1073445695/ 0xc00484c1) | Received an error from the WS-Trust endpoint. Note: WS-Trust is required for federated authentication. | Ensure that the network proxy isn’t interfering with and modifying the WS-Trust response.Event 1088 (Azure AD operational logs) would contain the server error code and error description from the WS-Trust endpoint. Common server error codes and their resolutions are listed in the next section. |
| AAD_CLOUDAP_E_HTTP_PASSWORD_URI_IS_EMPTY (-1073445749/ 0xc004848b) | The MEX endpoint is incorrectly configured. The MEX response doesn’t contain any password URLs. | Ensure that the network proxy isn’t interfering with and modifying the server response.Fix the MEX configuration to return valid URLs in response. |
| AAD_CLOUDAP_E_HTTP_CERTIFICATE_URI_IS_EMPTY (-1073445748/ 0xc004848C) | The MEX endpoint is incorrectly configured. The MEX response doesn’t contain any certificate endpoint URLs. | Ensure that the network proxy isn’t interfering with and modifying the server response.Fix the MEX configuration in the identity provider to return valid certificate URLs in response. |
| WC_E_DTDPROHIBITED (-1072894385/ 0xc00cee4f) | The XML response, from the WS-Trust endpoint, included a Document Type Definition (DTD). A DTD isn’t expected in XML responses, and parsing the response will fail if a DTD is included. Note: WS-Trust is required for federated authentication. | Fix the configuration in the identity provider to avoid sending a DTD in the XML response.Event 1022 (Azure AD analytics logs) will contain the URL that’s being accessed that’s returning an XML response with a DTD. |
Common server error codes:
| Error code | Reason | Resolution |
|---|---|---|
| AADSTS50155: Device authentication failed | Azure AD is unable to authenticate the device to issue a PRT.Confirm that the device hasn’t been deleted or disabled in the Azure portal. For more information about this issue, see Azure Active Directory device management FAQ. | Follow the instructions for this issue in Azure Active Directory device management FAQ to re-register the device based on the device join type. |
AADSTS50034: The user account Account does not exist in the tenant id directory | Azure AD is unable to find the user account in the tenant. | Ensure that the user is typing the correct UPN.Ensure that the on-premises user account is being synced with Azure AD.Event 1144 (Azure AD analytics logs) will contain the UPN provided. |
| AADSTS50126: Error validating credentials due to invalid username or password. | The username and password entered by the user in the Windows LoginUI are incorrect.If the tenant has password hash sync enabled, the device is hybrid-joined, and the user just changed the password, it’s likely that the new password hasn’t synced with Azure AD. | To acquire a fresh PRT with the new credentials, wait for the Azure AD password sync to finish. |
Common network error codes:
| Error code | Reason | Resolution |
|---|---|---|
| ERROR_WINHTTP_TIMEOUT (12002) ERROR_WINHTTP_NAME_NOT_RESOLVED (12007) ERROR_WINHTTP_CANNOT_CONNECT (12029) ERROR_WINHTTP_CONNECTION_ERROR (12030) | Common general network-related issues. | Events 1022 (Azure AD analytics logs) and 1084 (Azure AD operational logs) will contain the URL that’s being accessed.If the on-premises environment requires an outbound proxy, the IT admin must ensure that the computer account of the device can discover and silently authenticate to the outbound proxy. Get more network error codes. |
Step 4: Collect logs
Regular logs
- Go to https://aka.ms/icesdptool to automatically download a .cab file containing the Diagnostic tool.
- Run the tool and repro your scenario.
- For Fiddler traces, accept the certificate requests that pop up.
- The wizard will prompt you for a password to safeguard your trace files. Provide a password.
- Finally, open the folder where all the collected logs are stored, such as %LOCALAPPDATA%\ElevatedDiagnostics\numbers.
- Contact Support with contents of the latest .cab file.
Network traces
Note
When you’re collecting network traces, it’s important to not use Fiddler during repro.
- Run
netsh trace start scenario=internetClient_dbg capture=yes persistent=yes. - Lock and unlock the device. For hybrid-joined devices, wait a minute or more to allow the PRT acquisition task to finish.
- Run
netsh trace stop. - Share the nettrace.cab file with Support.
Known issues
- If you’re connected to a mobile hotspot or an external Wi-Fi network and you go to Settings > Accounts > Access Work or School, hybrid Azure AD-joined devices might show two different accounts, one for Azure AD and one for on-premises AD. This UI issue doesn’t affect functionality.
Ref: Troubleshoot hybrid Azure Active Directory-joined devices – Microsoft Entra | Microsoft Learn