In situations involving compromised user accounts simply disabling an account is often not sufficient to mitigate the threat especially if the account is actively being using to send SPAM/Phishing email or to download data. There are three supported ways of revoking an active user’s session in Office 365.
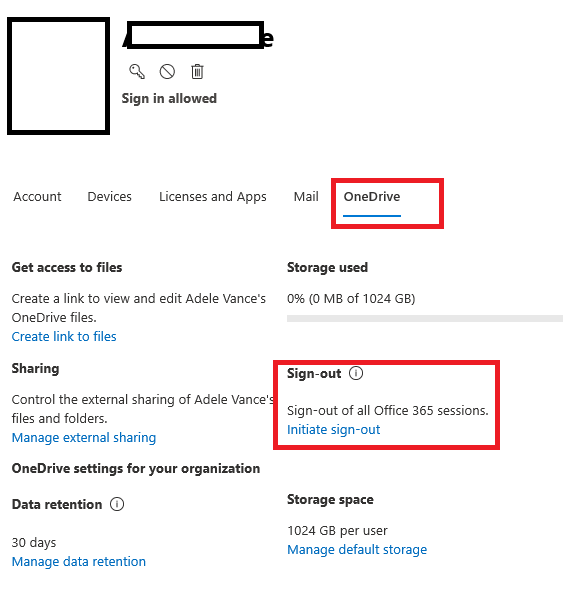
The first option is found in the Office 365 Admin Center under Home > Active Users. Select a user and expand the OneDrive Settings section for that user. Select “Initiate” to perform a one-time sign-out for that user that revokes active sessions across Office 365 services including Exchange Online.
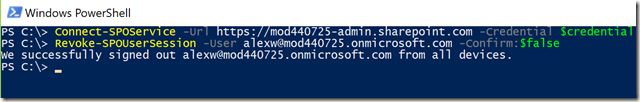
The second option to force logoff during an active user session in Office 365 to use Revoke-SPOUserSession cmdlet from the SharePoint Online PowerShell Module. This method is helpful for automating security incident response flows or when there is a need to revoke multiple users’ sessions.
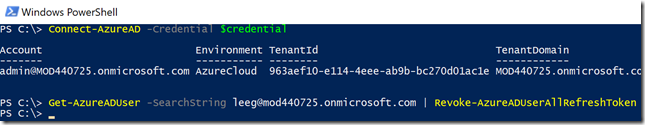
The third option to force a user sign-out extends beyond Office 365 services to all active user sessions in any Azure AD application (thanks to Micah Linehan for recommending to include this option in the list). The Revoke-AzureADUserAllRefreshToken cmdlet is available in the AzureAD V2 PowerShell Module and expires a user’s refresh token by modifying the user’s token validity period.
To force log off all users
Get-AzureADUser -all $true | revoke-azureaduserallrefreshtoken
Ref: https://learn.microsoft.com/en-gb/archive/blogs/educloud/how-to-kill-an-active-user-session-in-office-365
For other options, you can refer to the following article.