With 1Password Business, you can automate many common administrative tasks using 1Password SCIM bridge. It uses the System for Cross-domain Identity Management (SCIM) protocol to connect 1Password with your existing identity provider, like Azure Active Directory, JumpCloud, Okta, OneLogin, or Rippling.
Step 1: Add provisioning to your 1Password account
Before you can deploy 1Password SCIM Bridge, you’ll need to add the provisioning integration and get credentials for it. Click Get Started, sign in to your 1Password account, and follow the onscreen instructions.
If you see the details for an existing provisioning integration, you’ll need to deactivate it first. Click More Actions and choose Deactivate Provisioning.
After you complete the setup process, you’ll get a scimsession file and bearer token. Save them both in 1Password and save the scimsession file to your computer. You’ll need these to deploy the SCIM bridge and connect your identity provider.
IMPORTANT
The bearer token and scimsession file you receive during setup can be used together to access information from your 1Password account. You’ll need to share the bearer token with your identity provider, but it’s important to never share it with anyone else. And never share your scimsession file with anyone at all.
Step 2: Create and configure the Kubernetes cluster
2.1: Start creating a Kubernetes cluster
The SCIM bridge must be deployed to a cluster. To create a cluster:
- Sign in to your account on the Microsoft Azure portal.
- On the Azure portal menu or from the Home page, select “Create a resource”.
- Select Containers > Kubernetes Service.
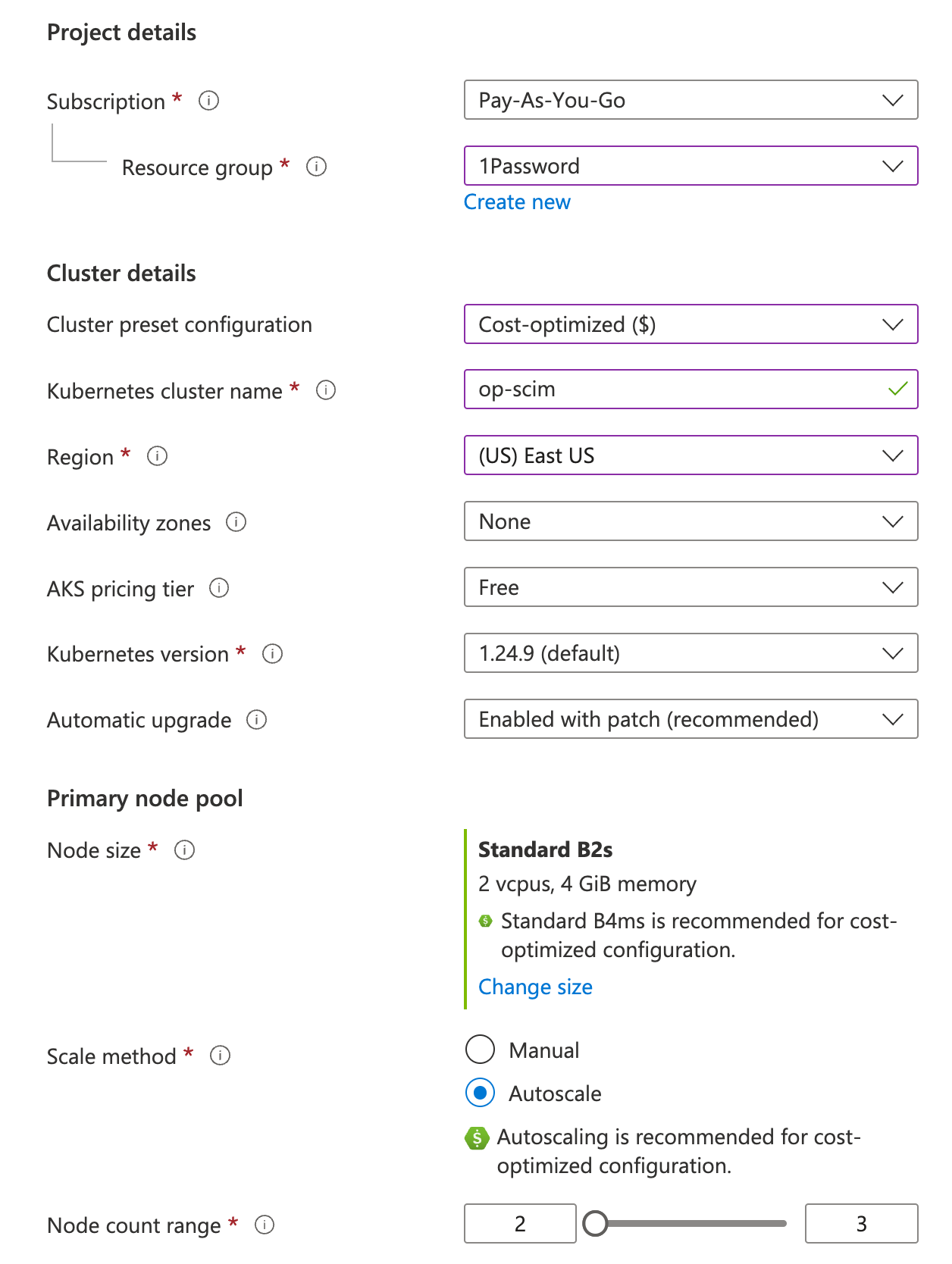
2.2: Configure your cluster
Configure your cluster using the following options. For all other options, you can use the provided defaults or choose your preferred options.
Project details:
- Resource group
Choose one, or click “Create new” and enter “1Password”.
Cluster details:
- Kubernetes cluster name
Enter “op-scim”.
Primary node pool:
- Node size
The SCIM bridge requires at least a “Standard B2s” VM size. - Scale method
Choose Autoscale. - Node count
The SCIM bridge requires at least 2 nodes.
After you’ve configured your cluster, click “Review + create”. It may take a moment. When you see “Validation passed”, click “Create”.
When you see “Your deployment is complete”, continue to the next step.
Step 3: Set up and deploy 1Password SCIM Bridge
3.1: Connect to your Kubernetes cluster
- Open your cluster on the Microsoft Azure portal.
- Click Connect at the top of the page.
- Click Open Cloud Shell to connect to the cluster.
3.2: Clone the scim-examples repository
All the configuration files you need to deploy the SCIM bridge are available in the scim-examples repository on GitHub.
Switch to the directory where you want to clone the repository, then run the following command:
git clone https://github.com/1Password/scim-examples.git
Switch to the Kubernetes directory in the cloned repository:
cd scim-examples/kubernetes
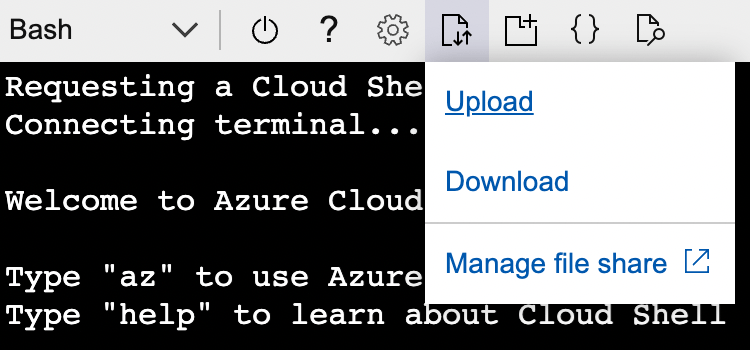
3.3: Upload your scimsession file
Before you create the Kubernetes Secret, upload your scimsession file to the Cloud Shell:
- Click the “Upload/Download files” button and choose Upload.
- Find the
scimsessionfile that you saved to your computer and choose it. - Make note of the upload destination, then click Complete.
3.4: Create the Kubernetes Secret
To create the Kubernetes Secret, run the following command:
- Bash:
kubectl create secret generic scimsession --from-file=scimsession=/home/$USER/scimsession - Powershell:
kubectl create secret generic scimsession --from-file=scimsession=/home/$Env:USER/scimsession
3.5: Deploy 1Password SCIM Bridge
1Password SCIM Bridge uses a Redis instance to store and cache your Let’s Encrypt TLS certificate. Deploy the configuration, 1Password SCIM Bridge, Redis, and the load balancer using the following command:
kubectl apply -f .
3.6: Create the DNS record
1Password SCIM Bridge requires a public DNS record on a domain that you manage. Before you create the DNS record, get the external IP address of the load balancer:
kubectl get services
If you don’t see the IP address in the External IP column, wait a few minutes and try again.
Add an A record that points to the public IP address for the load balancer. For example, if your domain is example.com, use scim.example.com.
TIP
All SCIM bridge traffic uses port 443. If you use Azure Firewall or are restricting ingress to 1Password SCIM Bridge, open port 443 for your Azure Kubernetes cluster. Let’s Encrypt requires ingress on port 443 to renew the TLS certificate every 60 days.
3.7: Configure and enable Let’s Encrypt
1Password SCIM Bridge uses a TLS certificate provided by Let’s Encrypt to secure communication with your identity provider.
Set the fully qualified domain name (FQDN) based on the DNS record you created in the last step (for example: scim.example.com) as the value for OP_LETSENCRYPT_DOMAIN:
kubectl set env deploy/op-scim-bridge OP_LETSENCRYPT_DOMAIN=scim.example.com
Step 4: Test your SCIM bridge
IMPORTANT
Before you connect the SCIM bridge to your identity provider, make sure that you can connect to the SCIM bridge:
- over a secured (HTTPS) connection
- with a valid TLS certificate
To check that the DNS has propagated and the SCIM bridge is deployed successfully, visit the domain you configured in the previous step in your browser. You’ll see a 1Password SCIM Bridge status page. Enter your OAuth bearer token to verify it’s correct.
Use your bearer token and domain (for example: scim.example.com) to test the connection to 1Password:
curl --header "Authorization: Bearer <bearer_token>" https://<domain>/scim/Users
If you see a list of the users in your 1Password account, your SCIM bridge is deployed correctly.
Step 5: Connect your identity provider to the SCIM bridge
IMPORTANT
If you’ve already been using 1Password Business, make sure the email addresses and group names in your 1Password account are identical to those in your identity provider.
- If anyone is using a different email address in 1Password, ask them to change it.
- If you have existing groups in 1Password that you want to sync with groups in your identity provider, adjust the group names in 1Password.
Because 1Password SCIM Bridge provides a SCIM 2.0-compatible web service that accepts OAuth bearer tokens for authorization, you can use it with a variety of identity providers.
USER GUIDE
Learn how to connect your identity provider:
Ref: Deploy 1Password SCIM Bridge on Azure Kubernetes Service